Lynis Enterprise Modules
This is the supporting documentation for Lynis Enterprise, with focus on the Lynis Control Panel and related modules. For the installation of Lynis there is the Installation Guide available.
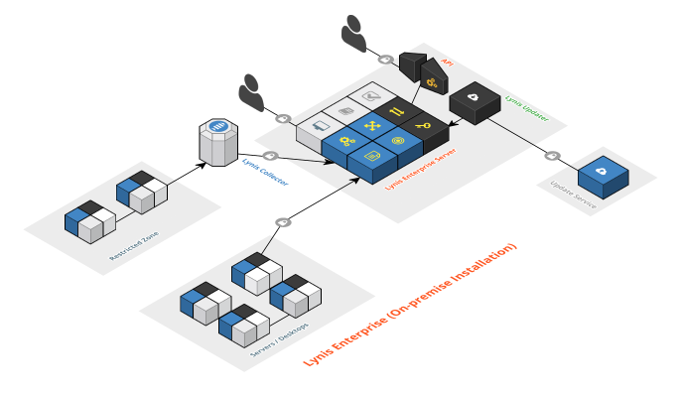
Lynis Enterprise - Software Architecture
System and Software Components for Lynis EnterpriseThis documentation focuses on the architecture of Lynis Enterprise and its components.As part of our open source vision, we like to openly share our knowledge. Please refer to the information below for additional guidance. If you are looking for downloads, visit our downloads section.
Abstract
Part I: Lynis EnterprisePart II: Lynis
Part III: Lynis Control Panel
Part I: Lynis Enterprise
1. Introduction
Lynis Enterprise is a software solution to help companies secure their IT environment, with focus on Unix based systems. Main focus of the product is achieving insights and system hardening. These insights are obtained due to measuring as much components as possible and creating security metrics. Regarding system hardening the focus is on security automation, to reduce the amount of work needed and simplify the activities required.
2. Software Components
Lynis Enterprise consists of open source components, including its open source scanning client Lynis. Enterprise users have access to most of the functionality, depending on the set-up and selected support package.
The solution has two levels visible to the user: data collection and presentation. Lynis and Lynis Collector are responsible for collecting data and distributing it to the central node. The Lynis Control Panel is responsible for presentating the data into actionable events and insights.
Protocols and Standards
For secure communication, including data exchange, the HTTPS protocol is being used. So only TCP port 443 needs to be opened towards the central portal. This can be done via firewall rules, or by using a proxy.
Lynis Enterprise overview
Part II: Lynis
Lynis Design
Lynis
In the Lynis download or package, the primary functionality is controlled by the binary 'lynis'. It is responsible for initializing all functions and performing a smoothless scan. For portability it is written in shell script (using /bin/sh). By default it will use only very common tools (e.g. awk, grep, ls and ps), to reduce the dependencies.
Functions
Most tests have repeating logic, so these are captured in smaller functions. These functions can be found in include/functions.
Binaries
Lynis is modular and determines on the fly what tests can be executed. It depends on the available binaries and their functionality (sometimes version specific). To obtain information about available binaries, Lynis runs a quick scan through all common directories to scan for them. This process can be found in include/binaries.
Profiles
By default Lynis uses the default.prf file to perform an audit. It is a profile, or template, to determine what kind of functions it should, or should not, perform during the audit.
Log Files
During the in-depth audits of Lynis, data is collected. To store this information, Lynis uses two files to split them appropriately.
- /var/log/lynis.log
- /var/log/lynis-report.dat
The log file /var/log/lynis.log consists of high detail information about the scan, including findings, command output and what activities are performed. This file is optional and can be set to redirect to /dev/null for example, to avoid creation of the file.
The file /var/log/lynis-report.dat is a storage container for mostly scan findings and data. It may be used for automated processing by the Lynis Enterprise solution.
Lynis Controls
Each audit control is made as small as possible. Usually it consists of a particular check, with an action. For example search for a configuration file and extract a particular setting. Another example would be gathering all running processes and store them for later processing. This method keeps tests simple and also simplifies follow-up by the user. Another benefit is that individual tests can be disabled, or searched for, on the website or in the log files.
Screen Output
The screen is used to give insights about the status of the scan and related findings. It can be seen as a portal for further exploration to harden the system.
Lynis Development
To make sure Lynis stays up-to-date and it tested properly, we opened up the development and share it on GitHub: Lynis.
Custom Tests
Extending the functionality of Lynis is surprisingly easy. Tests are created in shell script, which is a common language to system administrators. As Lynis is open source, you can check out the existing tests in the include directory. Next step is creating the file tests_custom and add your own tests to it. To prevent clashes with existing or new tests, use the CUST prefix for your test (e.g. CUST-1234).
Custom Plugins
Development of plugins is similar to creating your own tests. A quick way to start is copy an existing plugin and reuse logic and common functions. Ensure that your plugins has an unique ID, prefixed with CUST (e.g. CUST-1234).
Part II: Lynis Control Panel
5. Lynis Control Panel
Enterprise users have access to the Lynis Control Panel. This component enables central management, reporting and follow-up on findings. By centrally collecting all data, the software can do a better analysis on any possible weaknesses in security defenses and how to solve them.
6. SaaS versus On-Premise Installation
Depending on the size of the installation, we provide two options for storing and processing data: Software-as-a-Service (SaaS) or a self-hosted system within your data center. For both installations we support the latest available LTS version of Ubuntu Server.
When to use SaaS:
Suitable for most companies, especially smaller companies. As a customer you only have to keep Lynis up-to-date and let have upload the gathered
information.
When to consider On-Premise: This solution is best suited to companies with high security demands, many systems or complex network segmentation. As it requires more work to set-up and manage, we will look at your needs first to determine what configuration would be best suited.
7. Software Architecture
7.1. Central Management
All management of the Lynis clients is done centrally in the Control Panel.
7.2. Data Collection
The collected data via the client is send to the central node and presented in the Control Panel. The client itself has an upload function, or the data may be collected via an alternative method and uploaded by the Lynis Collector. The transmission of data is done via HTTPS.
7.3. Security Metrics
Security and related advice should be actionable. This can only be done with measured findings and scoring them. Lynis Enterprise provide security metrics and scored reports.
7.4. Dashboard
Most solutions use a dashboard to give a quick overview on the status. Lynis Enterprise comes with 3 built-in dashboards, tailored per business user:
- Business (Business owner)
- Operational (Security manager)
- Technical (Engineer)
Depending on the dashboard, risks and findings are differently reported, so each of the target audience members can take action.
7.5. Security Advice
Part of our goal is providing actionable steps to secure systems. Lynis Enterprise has controls stating why a finding needs attention. It includes the related risk, scoring and guidance to solve the finding. This module calculates the related effort, risk of implementation and help you preparing a change ticket (e.g. for ITIL based companies).
7.6. Hardening Snippets
To enhance your security defenses, the system has built-in hardening snippets. For users of configuration management tools like Puppet, we also provide related snippets. These snippets help you with continuous security monitoring and automatic hardening.
7.7. Reporting
Where most solutions give you a lot technical output, our solution focuses on actionable items. For example a prioritized report, limited to only a few items and scored. This way it is easy to start enhancing your security defenses and have security incorporated in your daily activities. Hardening and security are not a one-time event, but part of a continuous improvement cycle.